The objective of this tutorial is to show you how to integrate SuccessFactors with Azure Active Directory (Azure AD).
Integrating SuccessFactors with Azure AD provides you with the following benefits:
- You can control in Azure AD who has access to SuccessFactors
- You can enable your users to automatically get signed-on to SuccessFactors (Single Sign-On) with their Azure AD accounts
- You can manage your accounts in one central location – the Azure classic portal
Prerequisites
To configure Azure AD integration with SuccessFactors, you need the following items:
- A valid Azure subscription
- A tenant in SuccessFactors
Note:To test the steps in this tutorial, we do not recommend using a production environment.
Scenario description
The objective of this tutorial is to enable you to test Azure AD single sign-on in a test environment.
The scenario outlined in this tutorial consists of two main building blocks:
- Adding SuccessFactors from the gallery
- Configuring and testing Azure AD single sign-on
Adding SuccessFactors from the gallery
To configure the integration of SuccessFactors into Azure AD, you need to add SuccessFactors from the gallery to your list of managed SaaS apps.
To add SuccessFactors from the gallery, perform the following steps:
- In the Azure classic portal, on the left navigation panel, click Active Directory.

- From the Directory list, select the directory for which you want to enable directory integration.
- To open the applications view, in the directory view, click Applications in the top menu.
- Click Add at the bottom of the page.
5.On the What do you want to do dialog, click Add an application from the gallery.
![]()
6.In the search box, type SuccessFactors.
7.In the results panel, select SuccessFactors, and then click Complete to add the application.

Configuring and testing Azure AD single sign-on
The objective of this section is to show you how to configure and test Azure AD single sign-on with SuccessFactors based on a test user called “Britta Simon”.
For single sign-on to work, Azure AD needs to know what the counterpart user in SuccessFactors to an user in Azure AD is. In other words, a link relationship between an Azure AD user and the related user in SuccessFactors needs to be established.
This link relationship is established by assigning the value of the user name in Azure AD as the value of the Username in SuccessFactors.
To configure and test Azure AD single sign-on with SuccessFactors, you need to complete the following building blocks:
- Configuring Azure AD Single Sign-On – to enable your users to use this feature.
- Creating an Azure AD test user – to test Azure AD single sign-on with Britta Simon.
- Creating a SuccessFactors test user – to have a counterpart of Britta Simon in SuccessFactors that is linked to the Azure AD representation of her.
- Assigning the Azure AD test user – to enable Britta Simon to use Azure AD single sign-on.
- Testing Single Sign-On – to verify whether the configuration works.
Configuring Azure AD single sign-on
In this section, you enable Azure AD single sign-on in the classic portal and configure single sign-on in your SuccessFactors application.
To configure Azure AD single sign-on with SuccessFactors, perform the following steps:
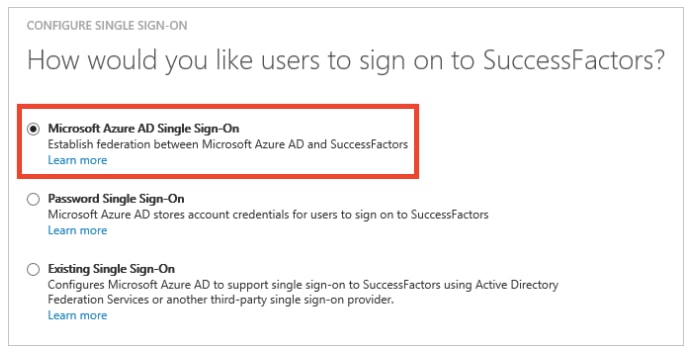
- In the Azure classic portal, on the SuccessFactors application integration page, click Configure single sign-on to open the Configure Single Sign On dialog.

- On the How would you like users to sign on to SuccessFactors page, select Microsoft Azure AD Single Sign-On, and then click Next.
- On the Configure App URL page, perform the following steps, and then click Next.
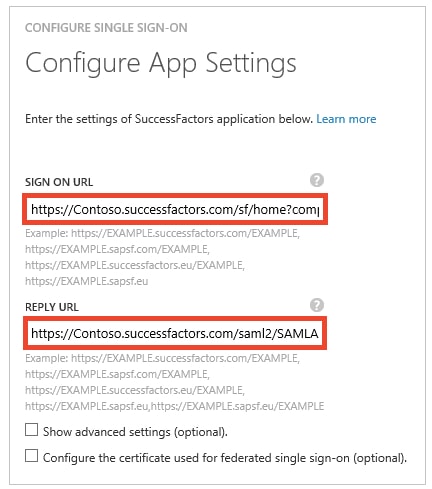
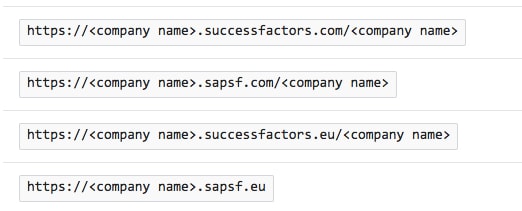
a. In the Sign On URL textbox, type a URL using one of the following patterns:
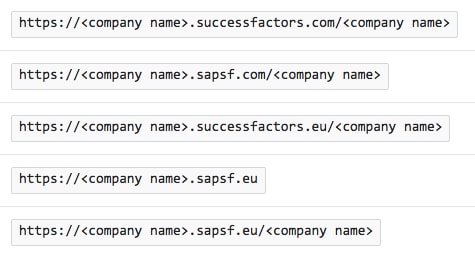
b. In the Reply URL textbox, type a URL using one of the following patterns:
c. Click Next.
Note : Please note that these are not the real values. You have to update these values with the actual Sign On URL and Reply URL. To get these values, contact SuccessFactors support team.
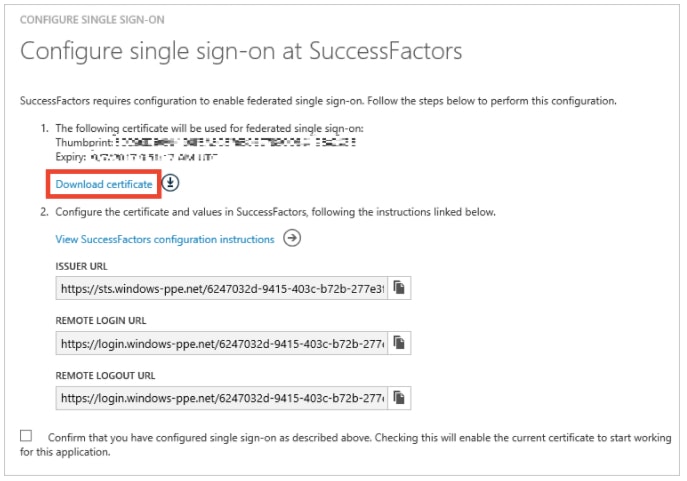
4. On the Configure single sign-on at SuccessFactors page, click Download certificate, and then save the certificate file locally on your computer.
5.In a different web browser window, log into your SuccessFactors admin portal as an administrator.
6.Visit Application Security and native to Single Sign On Feature.
7.Place any value in the Reset Token and click Save Token to enable SAML SSO.
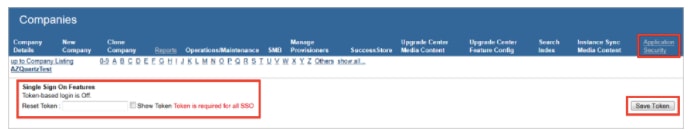
8.Native to below screenshot and perform the following actions.
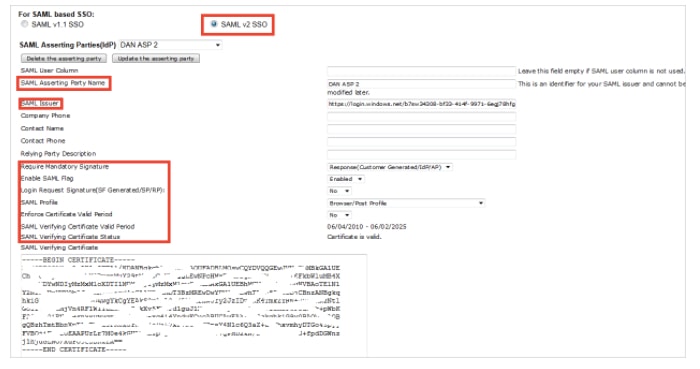
a. Select the SAML v2 SSO Radio Button
b. Set the SAML Asserting Party Name(e.g. SAml issuer + company name).
c. In the SAML Issuer textbox put the value of Issuer URL from Azure AD application configuration wizard.
d. Select Response(Customer Generated/IdP/AP) as Require Mandatory Signature.
e. Select Enabled as Enable SAML Flag.
f. Select No as Login Request Signature(SF Generated/SP/RP).
g. Select Browser/Post Profile as SAML Profile.
h. Select No as Enforce Certificate Valid Period.
i. Copy the content of the downloaded certificate file, and then paste it into the SAML Verifying Certificate textbox.
9.Navigate to SAML V2, and then perform the following steps:
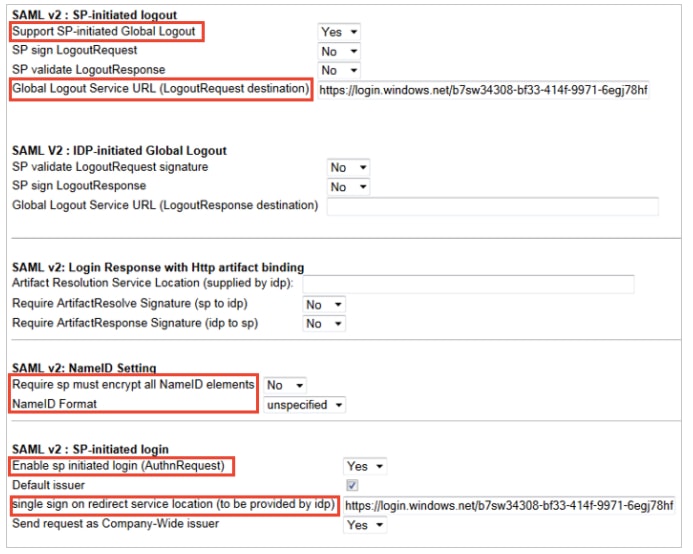 a. Select Yes as Support SP-initiated Global Logout.
a. Select Yes as Support SP-initiated Global Logout.
b. In the Global Logout Service URL (LogoutRequest destination) textbox put the value of Remote Logout URL from Azure AD application configuration wizard.
c. Select No as Require sp must encrypt all NameID element.
d. Select unspecified as NameID Format.
e. Select Yes as Enable sp initiated login (AuthnRequest).
f. In the Send request as Company-Wide issuer textbox put the value of Remote Login URLfrom Azure AD application configuration wizard.
10.Perform these steps if you want to make the login usernames Case Insensitive, .
a. Visit Company Settings(near the bottom).
b. select checkbox near Enable Non-Case-Sensitive Username.
c.Click Save.
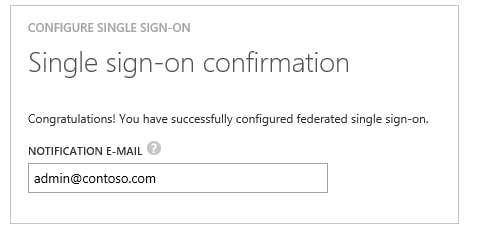
11.On the Azure classic portal, select the single sign-on configuration confirmation, and then click Complete to close the Configure Single Sign On dialog.
Creating an Azure AD test user
The objective of this section is to create a test user in the classic portal called Britta Simon.
To create a test user in Azure AD, perform the following steps:
- In the Azure classic Portal, on the left navigation pane, click Active Directory.

- From the Directory list, select the directory for which you want to enable directory integration.
- To display the list of users, in the menu on the top, click Users.

- On the Tell us about this user dialog page, perform the following steps:
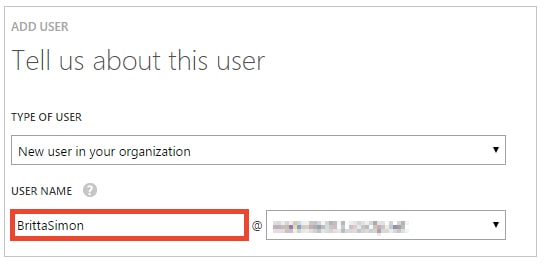 a. As Type Of User, select New user in your organization.b. In the User Name textbox, type BrittaSimon.c. Click Next.
a. As Type Of User, select New user in your organization.b. In the User Name textbox, type BrittaSimon.c. Click Next. - On the User Profile dialog page, perform the following steps:
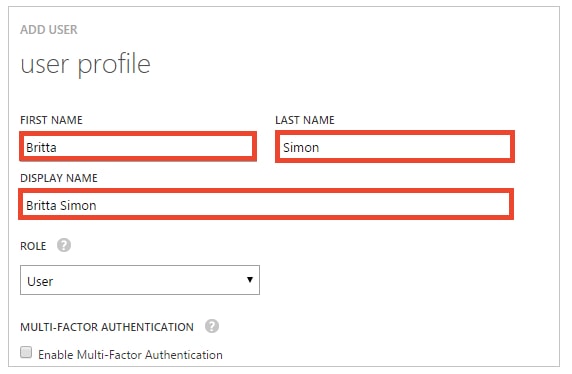 a. In the First Name textbox, type Britta.b. In the Last Name textbox, type, Simon.c. In the Display Name textbox, type Britta Simon.d. In the Role list, select User.e. Click Next
a. In the First Name textbox, type Britta.b. In the Last Name textbox, type, Simon.c. In the Display Name textbox, type Britta Simon.d. In the Role list, select User.e. Click Next - On the Get temporary password dialog page, click create.
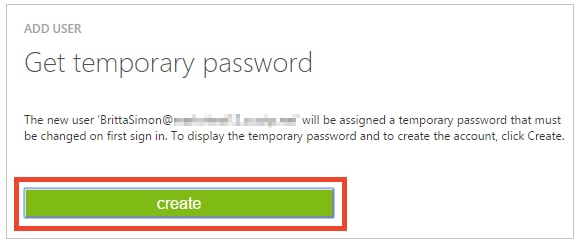
- On the Get temporary password dialog page, perform the following steps:
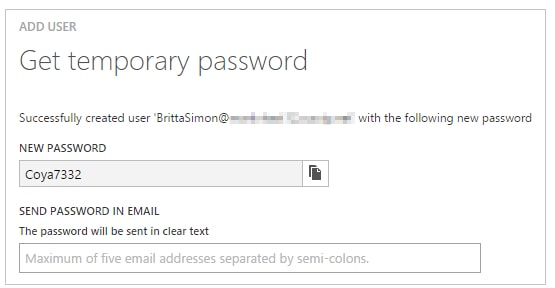 a. Write down the value of the New Password.b. Click Complete.
a. Write down the value of the New Password.b. Click Complete.
Creating a SuccessFactors test user
In order to enable Azure AD users to log into SuccessFactors, they must be provisioned into SuccessFactors.
In the case of SuccessFactors, provisioning is a manual task.To get users created in SuccessFactors, you need to contact the SuccessFactors support team.
Assigning the Azure AD test user
The objective of this section is to enabling Britta Simon to use Azure single sign-on by granting her access to SuccessFactors.
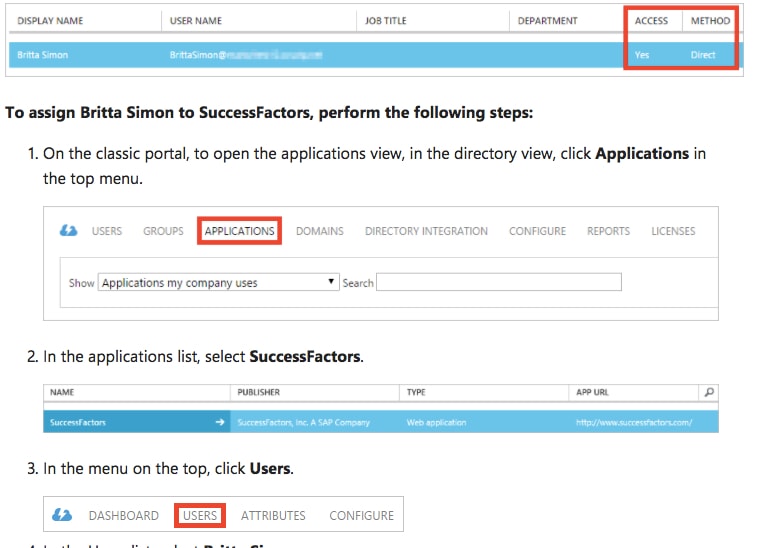 4.In the Users list, select Britta Simon.5.In the toolbar on the bottom, click Assign
4.In the Users list, select Britta Simon.5.In the toolbar on the bottom, click Assign
Testing single sign-on
The objective of this section is to test your Azure AD single sign-on configuration using the Access Panel.
When you click the SuccessFactors tile in the Access Panel, you should get automatically signed-on to your SuccessFactors application

Leave A Comment?
You must be logged in to post a comment.