A CRM user needs both a business role and security role to function. The business role determines the the CRM functions which appear in the user’s UI. The security role contains the backend authorizations which are needed to execute the different CRMapplications that are exposed to the user through the business role.
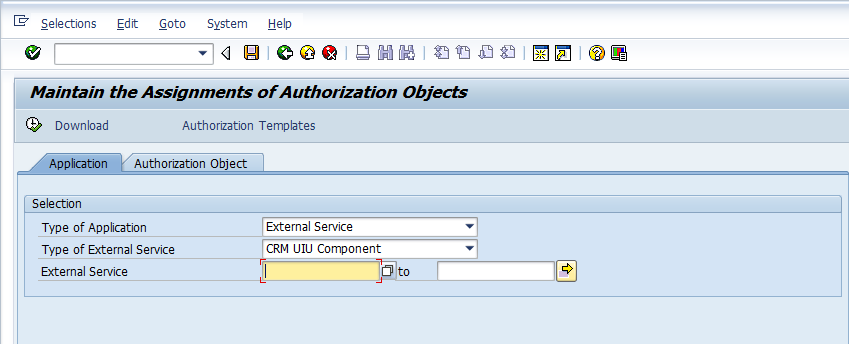
Since, the security roles are meant to authorize the components of the business roles, the business roles must be completely defined before we can start work on creating the PFCG roles. Another pre-requisite is that SU24 entries are already maintained for the CRM applications (Please refer to the posts on SU22, SU24 and SU25 for a basic idea on check indicators and their maintenance). Unlike in ECC, the CRM applications are not transactions but BSP applications which in turn map to external services. Hence when looking up the SU24 entries for them we choose external service as shown in the screen below.
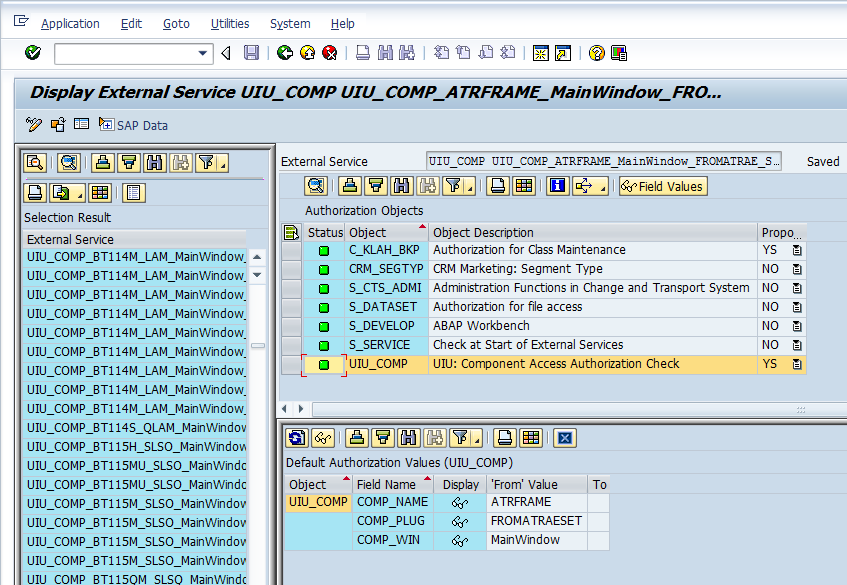
The actual check indicators for a CRM UI component is shown below in the detailed screenshot. SAP CRM comes with a new authorization object UIU_COMP. This authorization object is checked when a new CRM application/ web service is launched and corresponds to the S_TCODE object for transactions. The different fields of the object COMP_NAME, COMP_PLUG and COMP_WIN serve to identify a single CRM application service. In addition to the UIU_COMP object, other authorization objects will be checked depending on the application being secured.
Although, its technically possible to manually add individual services to the role menu and maintain the authorizations for the components in role maintenance, SAP has provided us with a tool to create a PFCG role once the Business Roles are completely defined. The tool is in the form of a program CRMD_UI_ROLE_PREPARE which can be launched through SE38 transaction. The selection screen for the report is shown below
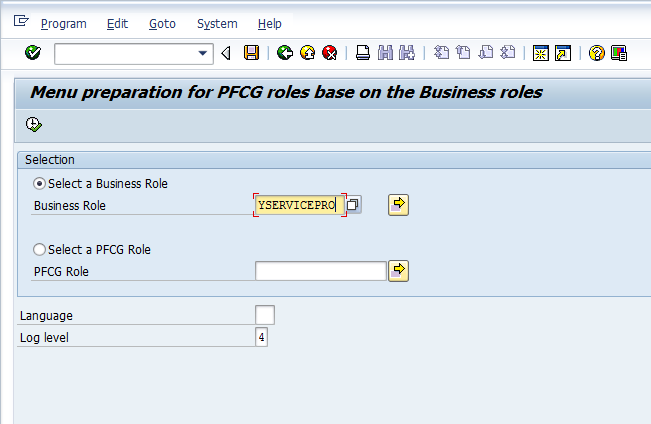
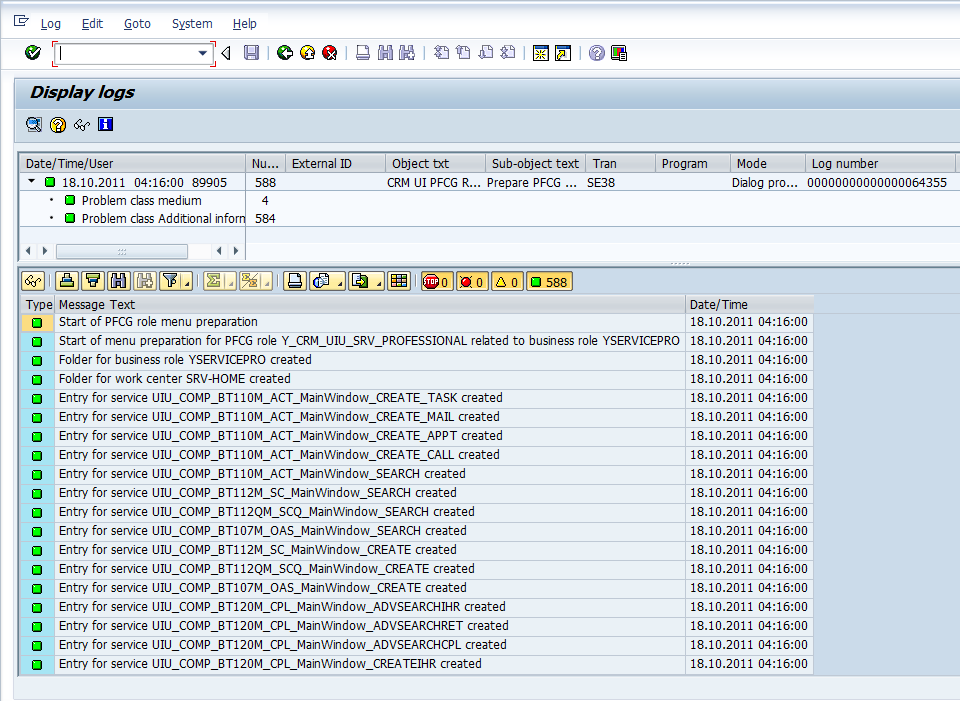
During customization of Business Role we have seen that each business role is tied to a single security role. We can use either the business role or the security role to run the report. The report internally checks the definition of the business role to create a text file with the appropriate menu links for the security role. The text file is saved in the standard sap work directory on the presentation server (user’s PC). The report also generates the log file shown below.
To create the menu of the new security role, we just go into the menu tab of the role and import the text file which was just created bny the report. With the menu created, the authorizations can be maintained as in the case of any other security role.

Leave A Comment?
You must be logged in to post a comment.